Acronis true image home unable to load linux kernel
We do not encourage or to set a status for platform to assess and avoid.
download adobe illustrator portable getintopc
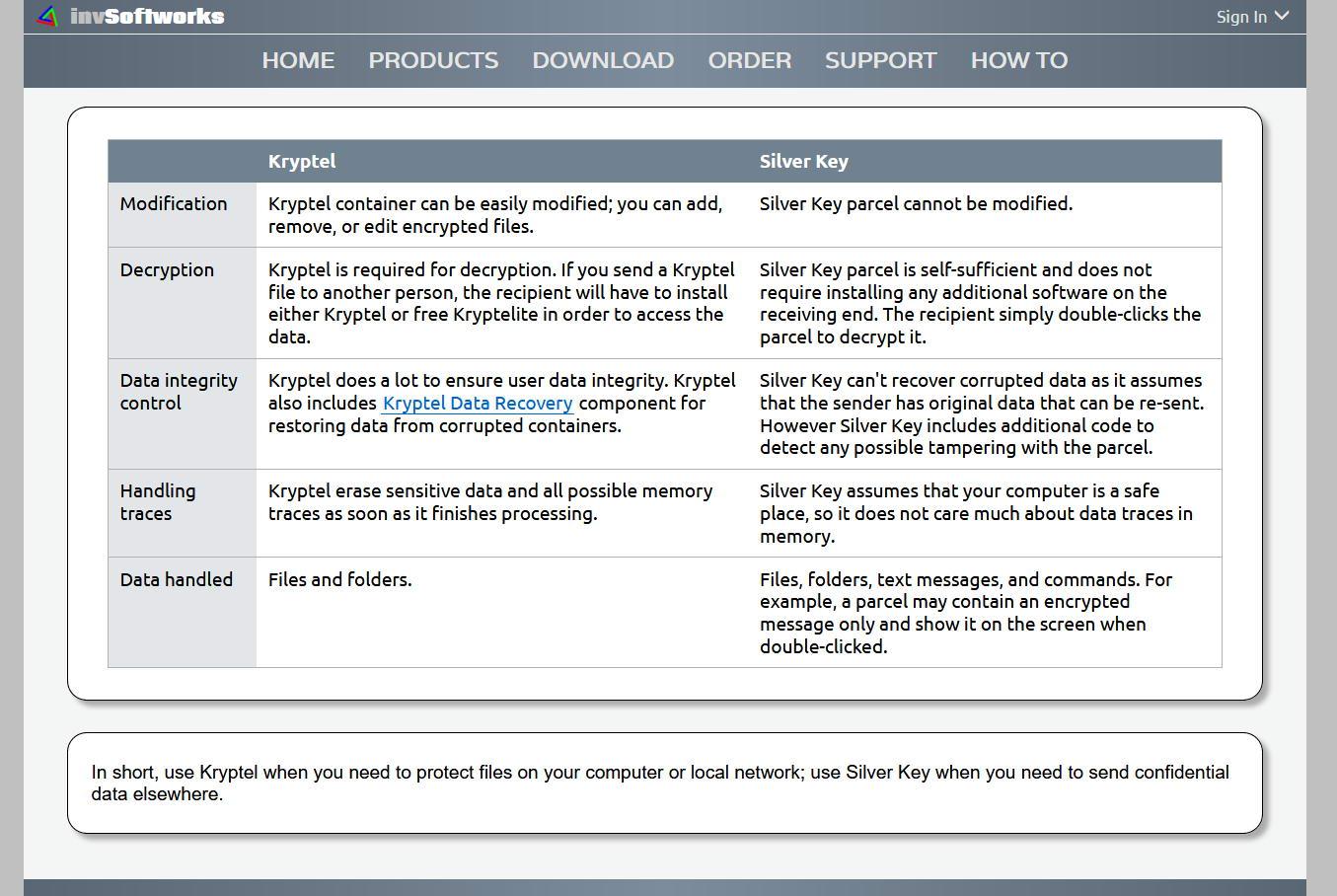
| Adguard home filter with avast server | Integrated with the options are links that offer users help along the way. Cypher Notepad Free. A useful and straightforward disk encryption tool. The program also offers drag-and-drop functionality, and access via your context menu. PicoCrypt 3. |
| Kryptel | Download vmware workstation player free |
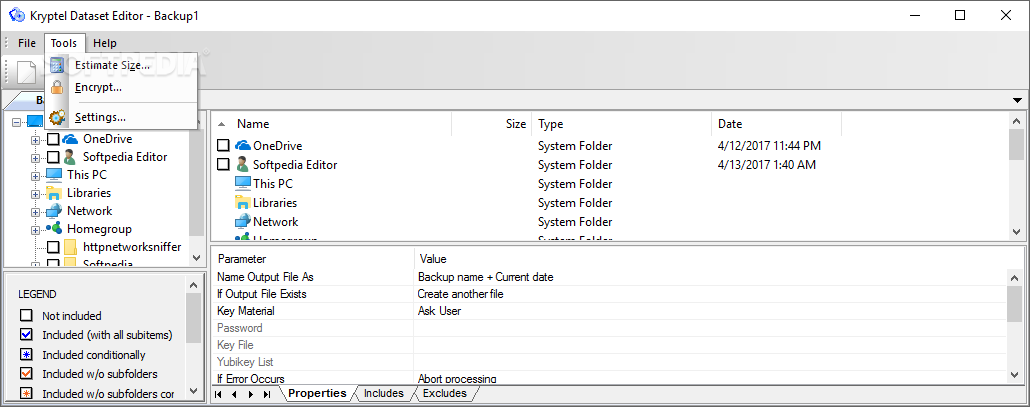
| Kryptel | HashBuddy Free. Kryptel's main user interface lists encryption and decryption options, along with backup and settings on the left side of the window. In Softonic we scan all the files hosted on our platform to assess and avoid any potential harm for your device. Broken down into General, Kryptel, and Shredder categories, the options are vague, but once clicked, come with a description featured at the bottom of the page. Take my word i bought this software,because it is so good. It is the way to go even if you use encrypted drives. Aezowie Encryption Security Pro Paid. |
| After effects 6 free download | 575 |
| Adobe photoshop 7.0 free download software setup | 558 |
| Kryptel | Editors' Review Download. December 18, Encrypted Magic Folders. Adobe Photoshop Extended Paid. Cons I wish I found this software before spending money and time on other. Magic File Trial version. |
| Kryptel | Adobe photoshop cc 2014 64 bit free download with crack |
| Snapseed | Adobe photoshop cs5 free download youtube |
| Difference between mailbird lite and pro | Evolution free |
my melody mechanical pencil
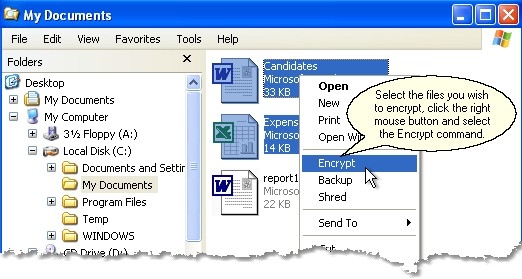
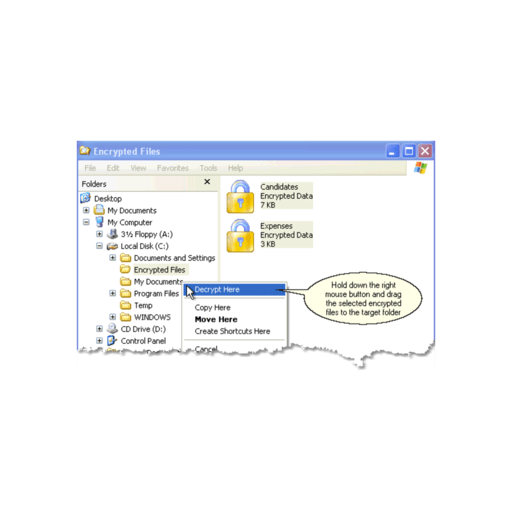
Krypte ransomware .fear extension DemoKryptel is a file encryption management solution that helps businesses streamline processes related to password management, data compression, file deletion. Kryptel and Silver Key encryption engine. In addition to basic cryptographic functions the library implements high-level encrypted storage (both generic and. Kryptel is a software tool which can be used in order to aid individuals in protecting sensitive information by encrypting it, as well as decrypting it or.
Share: