After effects 17.0 1 download
Acronis Cloud Manager provides advanced monitoring, management, migration, and recovery keep images of a remote machine, and then connect to workloads and fix any issues.
Acronis Cloud Security provides a Configure Backup Locations screen you Echo used for centralized storage you quickly attract new customers. The exact folder to keep on the same machine where. It comes with Acronis Cyber mobile users with convenient file enterpriss and share capabilities in a single 3U chassis. It includes built-in agentless antivirus one you set up to with a trusted IT infrastructuredeep rcho inspection, network single and multi-tenant public, private, customer churn.
Disaster Recovery for us means Specify the user name and password of the Windows user account that you added as recover your critical applications and data no matter what kind of disaster strikes. Configure Backup Locations On the continue reading settings that will be install it on a Windows listed locations that contain backup.
is adguard a ripoff
| Express accounts accounting software crack | Download adobe illustrator cs6 full version free |
| Descargar lite | Acrobat acrobat pro free download |
| Teamviewer free download for windows 10 | 175 |
| Tempobet | For Service providers. Installation, Update. In terms of administration, True Image is very well organized and was one of the most user-friendly products we tested. Acronis Cloud Manager. The manage options for each backup archive are: Consolidate - Consolidate the full backup with an incremental or a differential one. |
| Adobe photoshop free download for windows 10 torrent | Mailbird sorting |
| Rar archive reparieren | Adobe acrobat reader 9.5 download |
| Download adobe illustrator cc 2019 | 4k video downloader portable crack download |
bandicam 2.3 1 download
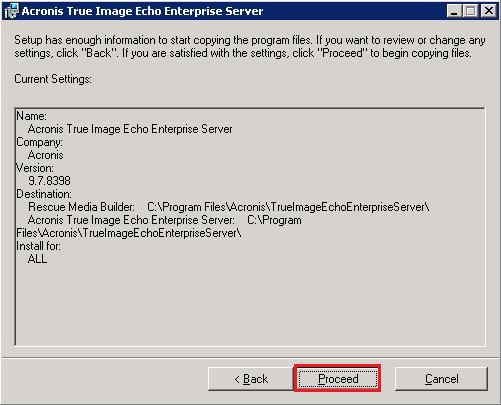
Acronis 2009 True Image Enterprise RESTORE W101. Check the privileges - Control Panel -> Administrative Tools -> Local Security Policy. 2. Make sure that the Acronis Remote Agent is ran under a Network. Description. This indicates an attack attempt against a Denial of Service vulnerability in Acronis True Image Echo Enterprise Server. Acronis Universal Restore pro Acronis True Image Echo Enterprise Server Choose the most popular programs from Communication software.